Monitoring visitor traffic is an important security, safety, and compliance practice for many facilities and organizations. Rather than using cumbersome manual logs, a visitor log template provides an easy way to track guests and generate records. To simplify visitor record keeping for reception areas, offices, schools, and more, we offer a customizable visitor log available for free download. This useful log template is provided as an editable PDF,Word and Excel type.
Users can add their company name, record visit details, print organized logs, and export the data. With this log, receptionists, administrators, and security staff can quickly record visitor names, entry/exit times, contact information, and any notes. Maintaining thorough visitor logs creates valuable documentation while providing an extra layer of protection. With our free professionally designed template, any organization can instantly create paper or digital logs to streamline visitor management.
Table of Contents
What Is A Visitor Log?
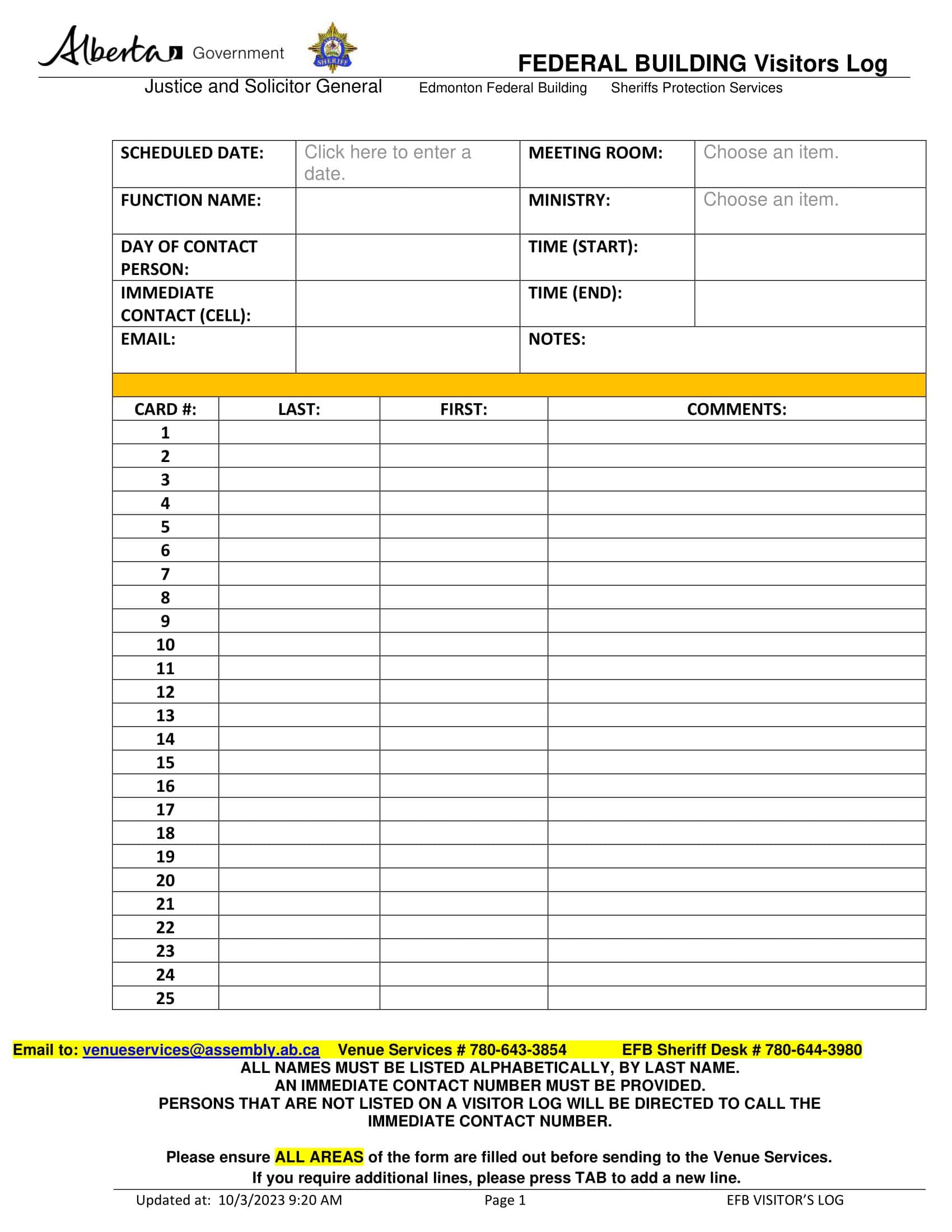
![Free Printable Visitor Log Templates [PDF, Word, Excel] School, Office 1 Visitor Log](https://www.typecalendar.com/wp-content/uploads/2023/10/Visitor-Log.jpg 1545w, https://www.typecalendar.com/wp-content/uploads/2023/10/Visitor-Log-232x300.jpg 232w, https://www.typecalendar.com/wp-content/uploads/2023/10/Visitor-Log-791x1024.jpg 791w, https://www.typecalendar.com/wp-content/uploads/2023/10/Visitor-Log-768x994.jpg 768w, https://www.typecalendar.com/wp-content/uploads/2023/10/Visitor-Log-1187x1536.jpg 1187w)
A visitor log is a document used to record information about guests, clients, contractors, and anyone else entering a facility or organization who is not a regular authorized employee. Visitor logs typically include fields to capture details like the visitor’s name, company/organization, the person they are meeting with, time of arrival and departure, vehicle/license if applicable, contact information, and purpose of visit.
Requiring visitors to sign in not only creates a record of who is on the premises, but it also serves safety purposes in case of emergency evacuation or if contact tracing is needed. Some facilities even require visitors to display ID badges. Maintaining thorough visitor logs provides security, a liability record, and adherence to regulations. They are an important tracking practice for monitoring stranger access.
Visitor Log Templates
A visitor log template is a useful tool for keeping track of guests that come to your home or office. The template provides a structured format to record relevant details about each visitor. This includes fields for basic information such as the date, visitor name, phone number, arrival and departure times.
The main benefit of using a template is consistency. With a structured template, the same information can be captured for every visitor that comes. This makes it easy to retrieve visitor history and details if needed. The format also prompts you to gather key data points that may be easily forgotten without a template.
Customizable visitor log templates allow you to add or remove fields as needed. Additional details could include the purpose of the visit, who the visitor is meeting with, and any other notable information. Beyond gathering data, a visitor log promotes security by documenting who has been to your location and when. This creates accountability in case any issues arise. Maintaining thorough visitor logs demonstrates professionalism and organization.
The Importance of Keeping a Visitors Log
A visitor’s log, sometimes known as a sign-in sheet or visitor’s book, is a record of individuals who visit a particular establishment, office, or event. This seemingly simple administrative tool holds significant importance for various reasons, ranging from security concerns to regulatory compliance. Here’s a detailed look at why keeping a visitor’s log is essential:
Security and Monitoring:
- Traceability: In case of any security breaches or incidents, a visitor’s log provides a record of all individuals who were present at a given time. This makes it easier to trace any suspicious activity or conduct investigations.
- Controlled Access: Requiring visitors to sign in can deter potential intruders or unauthorized individuals from accessing the premises.
- Awareness: Staff or security personnel can be alerted to the presence of visitors, ensuring they monitor unfamiliar individuals.
Emergency Procedures:
- Headcount: In emergency situations, like fires or natural disasters, a visitor’s log provides an accurate count of the individuals on the premises. This is vital for ensuring everyone is accounted for during evacuations or rescue operations.
- Contact Information: The log often includes contact details, which can be crucial if there’s a need to communicate with visitors post-incident or inform their emergency contacts.
Legal and Regulatory Compliance:
- Proof of Visit: In some industries, especially those under strict regulatory scrutiny, it’s vital to have a record of all visitors. This can serve as evidence in any legal disputes or when demonstrating compliance to regulatory bodies.
- Data Retention: Some regulations might mandate the retention of visitor data for a specific duration. A log ensures this data is systematically stored and can be accessed when required.
Business Insights and Management:
- Traffic Patterns: Understanding the frequency and timing of visits can help businesses make informed decisions, such as allocating resources or staff during peak times.
- Feedback: Some visitor’s logs have a section for comments, providing a platform for feedback or reviews which can be useful for continuous improvement.
- Networking: Having a record of business visitors can be a tool for relationship management and future outreach.
Privacy and Confidentiality:
- Nondisclosure Agreements (NDAs): For businesses that handle sensitive information, having visitors sign an NDA upon entry, often incorporated within the log process, ensures protection against information leaks.
- Confidentiality Assurance: In settings like medical clinics or counseling centers, logs can be structured to maintain patient or client anonymity while still recording visits.
Professionalism and First Impressions:
- Organized Approach: A systematic sign-in process can portray a company as organized and professional, making a positive impression on visitors.
- Expectation Setting: The act of signing in can also set the tone for the visit, emphasizing the importance of appointments or scheduled meetings.
Community Engagement and Networking:
- Alumni or Guest Tracking: For institutions like schools or universities, a visitor’s log can track alumni or guest speaker visits, fostering community engagement.
- Networking Opportunities: Businesses can identify potential partners, investors, or other stakeholders through their visitor records.
How to Design Your Visitor Log: A Step-by-Step Guide
Designing an effective visitor log requires thought and consideration, ensuring it captures all the necessary information while being user-friendly. Here’s a guide to help you create a functional visitor log:
Step 1: Determine Your Needs
Before starting, ask yourself why you need the visitor log. Is it for security, regulatory compliance, business insights, or all of these reasons? Your needs will dictate what information to capture.
Step 2: Choose a Format
Decide whether your log will be a physical book, a printed sheet, or a digital system. While traditional logs use pen and paper, many modern establishments now utilize digital sign-in systems, which can offer more features and greater security.
Step 3: Design the Layout
For a physical or printed log:
- Use a clean, grid-like layout.
- Ensure columns are spacious enough for visitors to write legibly. For digital logs:
- Design an intuitive interface.
- Make sure there’s a clear flow from one field to the next.
Step 4: Decide on Essential Fields
At a minimum, include the following:
- Visitor’s full name
- Purpose of visit
- Date and time of entry
- Time of departure
Step 5: Add Additional Fields as Necessary
Depending on your needs, consider including:
- Contact number or email
- Company or organization affiliation
- Name of the person being visited
- Signature (especially if agreeing to terms or NDAs)
- Comments or feedback section
Step 6: Include Security Measures (For Digital Logs)
- Implement password protection or other security features.
- Ensure data encryption for sensitive information.
- Provide an option for photo capture or ID scanning.
Step 7: Pilot Test
Before fully implementing, test your log design:
- For paper logs, print a few pages and ask colleagues to fill them out for feedback.
- For digital systems, do a trial run with a small group, gathering input on usability.
Step 8: Revise as Necessary
Based on feedback, make necessary changes to the design, fields, or layout.
Step 9: Implement and Train
- Place your physical logbook or sign-in sheets at the entrance or reception area.
- For digital systems, set up terminals or tablets at key entry points.
- Train reception or security staff on its use, ensuring they understand its importance and can guide visitors as needed.
Step 10: Regularly Review and Update
- Periodically review entries for consistency and completeness.
- Update your log design as your needs evolve or if you notice recurrent issues.
Step 11: Store and Archive
- For paper logs, once filled, store them in a secure location.
- For digital logs, regularly back up data and ensure long-term storage solutions, especially if needed for compliance or record-keeping.
Step 12: Ensure Privacy Compliance
- If collecting personal data, be aware of privacy regulations in your jurisdiction. Inform visitors about how their data will be used and stored.
- Regularly purge old data that’s no longer necessary to keep, especially if it contains personal details.
Conclusion
A well-curated visitor log is more than a mere administrative tool—it stands as a testament to an organization’s commitment to security, professionalism, and efficient record-keeping. As businesses and institutions evolve in the digital age, so does the importance of having an effective sign-in mechanism.
Recognizing the diverse needs of our readers, we’ve incorporated free printable blank Visitor Log templates, allowing for a customizable and immediate solution. Whether you’re a small startup or a sprawling institution, these templates serve as a foundation, ensuring that every guest’s visit is documented with precision. So, as you prioritize safety, compliance, and insight generation in your space, our versatile Visitor Log templates are here to simplify the process, letting you focus on what truly matters—your core operations and guests.
FAQs
How should I ensure privacy with visitor logs?
Ensure that the collected data aligns with privacy regulations in your jurisdiction. Store logs securely, limit access to authorized personnel only, and dispose of or delete records after they’re no longer required. Inform visitors about how their data will be used and stored.
How long should I retain the records in a visitor log?
Retention depends on the organization’s policy, industry standards, and local regulations. While some might retain logs for a few weeks or months, others, particularly those in regulated industries, may need to keep them for several years.
Can visitor logs be used as legal evidence?
Yes, in certain situations, visitor logs can serve as evidence, especially in cases where it’s crucial to establish the presence (or absence) of an individual at a specific time and date.
Should visitors be informed about the purpose of logging their details?
Absolutely. It’s best practice (and often a legal requirement) to inform visitors why their details are being recorded. This can be done verbally, with signage, or as a printed notice on the log itself.
Are there any specific features to look for in a digital visitor log system?
Look for features like data encryption, integration with other security systems, easy search and retrieval options, real-time updates, photo or ID capture capabilities, and compliance with privacy regulations.
Can visitor logs help with contact tracing in health-related situations?
Yes, especially in the context of global health concerns, visitor logs can play a pivotal role in contact tracing, helping health officials track down individuals who might have come into contact with a contagious person.







































![Free Printable Roommate Agreement Templates [Word, PDF] 2 Roommate Agreement](https://www.typecalendar.com/wp-content/uploads/2023/06/Roommate-Agreement-150x150.jpg)
![Free Printable Credit Card Authorization Form Templates [PDF, Word, Excel] 3 Credit Card Authorization Form](https://www.typecalendar.com/wp-content/uploads/2023/06/Credit-Card-Authorization-Form-150x150.jpg)
![Free Printable Stock Ledger Templates [Excel,PDF, Word] 4 Stock Ledger](https://www.typecalendar.com/wp-content/uploads/2023/08/Stock-Ledger-150x150.jpg)
