In today’s digital age, the protection of sensitive information is of the utmost importance for businesses and organizations of all sizes. A comprehensive security policy is essential for ensuring the confidentiality, integrity, and availability of sensitive data, as well as for protecting against cyber threats and compliance with industry regulations.
This article will provide an overview of the key elements that should be included in a security policy, and explain the steps that organizations can take to develop, implement, and maintain an effective security program.
Table of Contents
Security Policy Templates
Safeguard your organization’s sensitive data and protect against cybersecurity threats with our comprehensive collection of Information Security Policy templates. These templates provide a robust framework for establishing clear guidelines, best practices, and protocols to ensure the confidentiality, integrity, and availability of information assets. Whether you’re a small business, large corporation, or government agency, our templates cover a wide range of information security domains, including access control, data classification, incident response, network security, and more.
Customize the templates to align with your organization’s specific needs, industry regulations, and compliance requirements. By implementing a strong Information Security Policy, you can instill a culture of security, mitigate risks, and demonstrate your commitment to protecting sensitive information. Download now and fortify your organization’s defenses with our professionally designed Information Security Policy templates.
What is a Security Policy?

A security policy is a set of guidelines and procedures that help an organization protect its sensitive information and assets from unauthorized access, disclosure, alteration, and destruction. These guidelines and procedures can include rules for physical and digital access control, incident response, and compliance with legal and regulatory requirements.
A security policy can also help an organization establish a culture of security, where employees are aware of their responsibilities for protecting sensitive information and are trained to identify and report potential threats.
Major types of security policy
There are several different types of security policies, each with a specific focus or purpose. Some common types of security policies include:
Information security policy: This type of policy focuses on the protection of sensitive information and data, such as personal data, financial information, and trade secrets. It includes guidelines for data classification, encryption, access controls, and incident response.
Network security policy: This type of policy focuses on securing an organization’s network infrastructure, including routers, switches, and servers. It includes guidelines for firewalls, intrusion detection and prevention systems, and virtual private networks (VPNs).
Endpoint security policy: This type of policy focuses on securing the devices that connect to an organization’s network, such as computers, laptops, and mobile devices. It includes guidelines for anti-virus and anti-malware software, and data encryption on endpoint devices.
Incident response policy: This type of policy focuses on how an organization will respond to security incidents, such as data breaches, cyber attacks, and natural disasters. It includes guidelines for incident reporting, investigations, and recovery procedures.
Compliance policy: This type of policy is written to ensure the organization is in compliance with regulatory requirements such as GDPR, HIPAA, PCI-DSS, SOC-2 etc.
Physical security policy: This type of policy focuses on the physical security of an organization’s facilities and assets, such as CCTV, keycard access controls, alarm systems, and emergency response procedures.
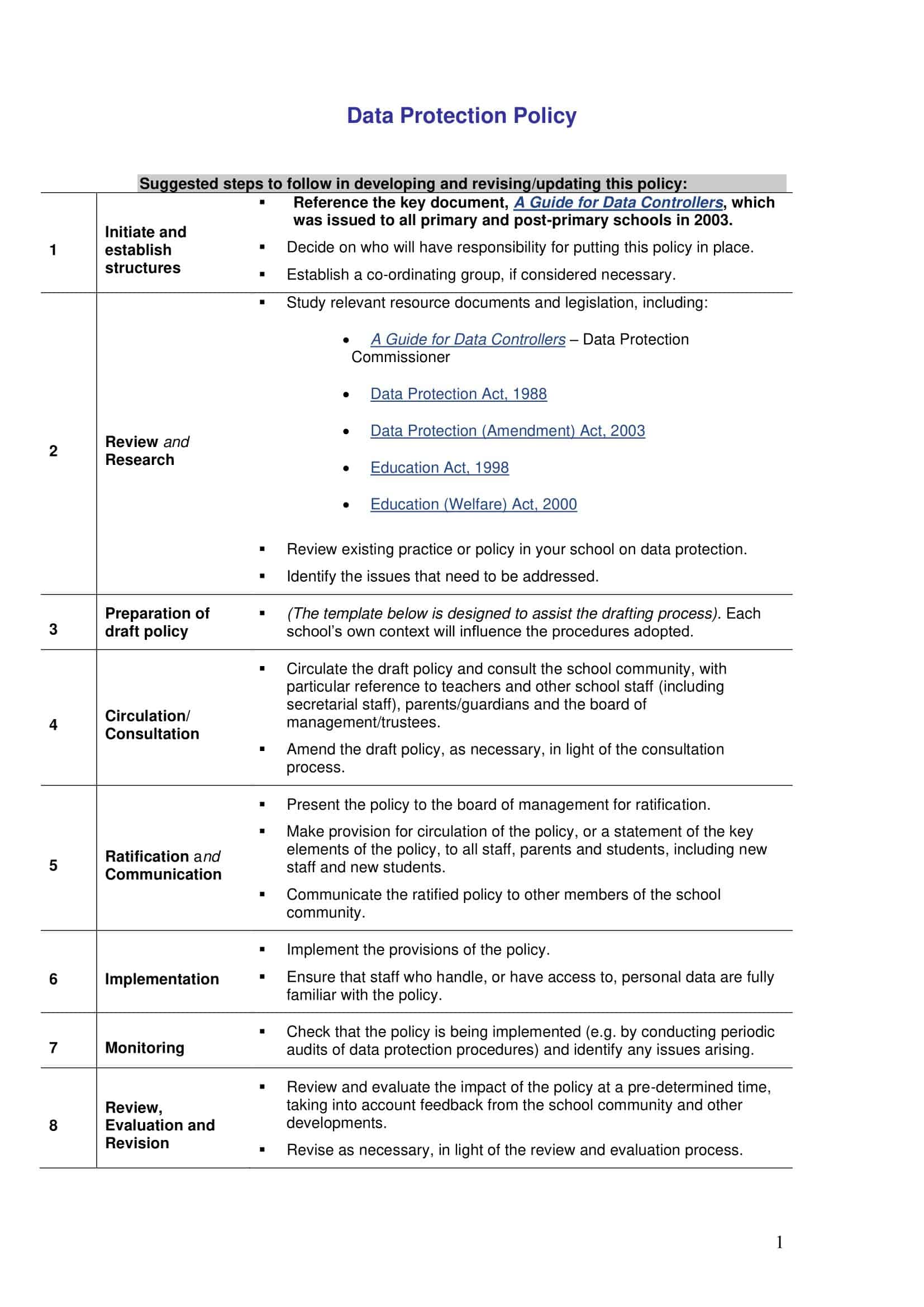
Main elements of a security policy
A security policy template typically includes the following elements:
Introduction: A brief overview of the purpose and scope of the security policy, including the organization’s security objectives and the areas and systems that the policy applies to.
Roles and Responsibilities: A description of the roles and responsibilities of different employees and teams in implementing and enforcing the security policy, including the roles of security officer, management, and employees.
Standards, guidelines and procedures: Specific technical and procedural requirements for securing the organization’s information and systems, such as authentication methods, software configuration, access controls, and incident response.
Physical and Environmental Security: Guidelines for securing the organization’s physical premises and assets, such as CCTV, access controls, alarm systems, and emergency response procedures.
Network and Communication Security: Guidelines for securing the organization’s networks and communications, such as firewalls, intrusion detection and prevention systems, and virtual private networks (VPNs).
Incident Response and Business Continuity: Procedures for responding to security incidents, including incident reporting, investigations, and recovery procedures, as well as plans for ensuring business continuity in the event of an incident.
Compliance: A statement of the organization’s compliance with relevant laws, regulations and industry standards such as GDPR, HIPAA, PCI-DSS, SOC-2 etc.
Review and Maintenance: A plan for regularly reviewing and updating the security policy, including procedures for reporting noncompliance and taking corrective action, as well as a process for training employees on the security policy and its associated procedures.
It’s important to note that depending on the organization, the types of assets and data it must protect, it could contain more or less than the above, but the above should be considered as a minimum. The security policy should be reviewed on regular basis, to ensure that it stays current with the threat landscape, emerging risks and regulations.
Benefits of Security Policy
There are several ways that organizations can benefit from using a security policy:
Protecting sensitive information: A security policy can help organizations protect their sensitive information and assets from unauthorized access, disclosure, alteration, and destruction. By providing guidelines and procedures for data classification, encryption, access controls, and incident response, organizations can ensure that their sensitive information is kept confidential and secure.
Compliance with regulations: A security policy can help organizations meet regulatory requirements for data protection and security. For example, many organizations are required to comply with laws such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) in order to protect personal data and health information.
Reducing risk: A security policy can help organizations identify and mitigate potential security risks, such as threats to network security, endpoint security, and incident response. By providing guidelines and procedures for securing networks and devices, organizations can reduce the likelihood of a security incident occurring.
Improving incident response: Having a well-defined incident response policy can help organizations quickly and effectively respond to security incidents, such as data breaches or cyber attacks. This can reduce the impact of an incident on the organization and its customers, and ensure that appropriate actions are taken to prevent similar incidents in the future.
Improving Employee Awareness: By providing training and awareness programs based on the security policy, organizations can increase employees’ awareness of security risks and best practices for protecting sensitive information. This can help reduce the risk of human error, such as employees falling prey to phishing emails or inadvertently sharing sensitive information.
Maintaining Business Continuity: Security policy also contains guidelines for ensuring business continuity in the event of an incident, this helps the organization to continue its operation and minimize interruption.
Saving Costs: By implementing a security policy, organizations can save costs by reducing the need for expensive security technologies and services, as well as by avoiding potential legal and regulatory fines and penalties.
Building Reputation: A comprehensive security policy can help organizations build trust and credibility with their customers and partners by demonstrating their commitment to protecting sensitive information and complying with industry standards.
How to create a powerful security policy
Creating a security policy can seem like a daunting task, but it doesn’t have to be. By following a systematic approach and involving key stakeholders throughout the process, organizations can develop a comprehensive and effective security policy that meets their unique needs.
Define the scope
The first step in creating a security policy is to define the scope of the policy. This includes identifying the areas and systems that the policy applies to, such as networks, systems, applications, and data. It’s important to ensure that the scope of the policy is sufficient to protect all of the organization’s sensitive information and assets.
Assess risk
The next step is to conduct a risk assessment to identify potential threats and vulnerabilities. This can include analyzing the organization’s existing security controls, as well as identifying new threats and risks that the organization may be exposed to. The outcome of the risk assessment will inform the security objectives and the standards, guidelines and procedures that should be included in the policy.
Define Security Objectives
Based on the outcomes of the risk assessment, organizations need to define its security objectives. These objectives should be specific, measurable and achievable. The objectives should be aligned with the organization’s overall business goals and objectives.
Determine Roles and Responsibilities
Organizations need to determine the roles and responsibilities of different employees and teams in implementing and enforcing the security policy. This includes identifying a security officer or team to lead the development and implementation of the policy, as well as the roles and responsibilities of management and employees.
Develop Standards, guidelines and procedures
After identifying the risks and objectives, organizations need to develop the specific technical and procedural requirements for securing the organization’s information and systems, such as authentication methods, software configuration, access controls, and incident response procedures. Organizations should consider utilizing industry standards and best practices when developing these guidelines.
Develop Physical and Environmental Security
Organizations need to develop guidelines for securing the organization’s physical premises and assets, such as CCTV, access controls, alarm systems, and emergency response procedures.
Develop Network and Communication Security
Organizations need to develop guidelines for securing the organization’s networks and communications, such as firewalls, intrusion detection and prevention systems, and virtual private networks (VPNs).
Develop Incident Response and Business Continuity
Organizations need to develop procedures for responding to security incidents, including incident reporting, investigations, and recovery procedures, as well as plans for ensuring business continuity in the event of an incident.
Compliance
Organizations need to include a statement of the organization’s compliance with relevant laws, regulations and industry standards such as GDPR, HIPAA, PCI-DSS, SOC-2 etc.
Review and Maintenance
Organizations need to develop a plan for regularly reviewing and updating the security policy, including procedures for reporting noncompliance and taking corrective action, as well as a process for training employees on the security policy and its associated procedures.
Implementation and Communication
Once the policy is developed, organizations need to communicate it to all relevant stakeholders and ensure that the policy is understood, implemented and followed by all employees. Organizations should ensure that employees are provided with appropriate training and awareness programs, and that any new employees receive the necessary training as soon as they join.
Regular review and update
It is important to regularly review and update the security policy in light of emerging threats, risks, and regulations, and to adapt the policy to reflect changes within the organization. Organizations should establish a schedule for reviewing and updating the security policy, and should involve key stakeholders in the review process.
It’s important to keep in mind that creating a security policy is an ongoing process, and not a one-time task.
FAQs
Why do organizations need a security policy?
Organizations need a security policy to protect their sensitive information and assets, comply with legal and regulatory requirements, and reduce the risk of security incidents. A security policy can also help organizations establish a culture of security and improve incident response.
How should organizations implement their security policy?
Organizations should implement their security policy in a phased approach, starting with a pilot implementation, testing the policy and procedures, and then rolling it out to the entire organization. It’s important to ensure that all employees are aware of the policy and have received the appropriate training and awareness programs. Organizations should also regularly review and update the policy to ensure that it stays current with emerging threats, risks and regulations.
Can a security policy be customized?
Yes, security policies can be customized to meet the unique needs of an organization. Organizations should consider their specific risks, assets and compliance requirements when creating a security policy and make sure it’s tailored to their business.
How should an incident be handled in accordance with the security policy?
Organizations should have an incident response plan in place, as part of their security policy. The incident response plan should include procedures for reporting, investigating and recovering from security incidents. The incident response team should follow the plan and take the necessary actions to minimize the impact of the incident. They should also conduct a post-incident review to evaluate the incident, identify areas of improvement, and update the incident response plan accordingly.
How can organizations ensure compliance with security policy?
Organizations can ensure compliance with the security policy by regularly monitoring compliance and taking corrective action in case of non-compliance. They can also provide employees with training and awareness programs to help them understand and comply with the policy. Organizations should also regularly review and update the policy to ensure that it stays current with regulatory changes and emerging threats.
How can a security policy be communicated and enforced within an organization?
A security policy should be communicated to all relevant stakeholders in the organization and understood by all employees. It should be easily accessible and kept up to date. Organizations should also provide employees with training and awareness programs and ensure they understand and comply with the policy. The policy should be enforced by management and the security team and any non-compliance should be reported and dealt with appropriately.

























































![Free Printable Roommate Agreement Templates [Word, PDF] 1 Roommate Agreement](https://www.typecalendar.com/wp-content/uploads/2023/06/Roommate-Agreement-150x150.jpg)
![Free Printable Credit Card Authorization Form Templates [PDF, Word, Excel] 2 Credit Card Authorization Form](https://www.typecalendar.com/wp-content/uploads/2023/06/Credit-Card-Authorization-Form-150x150.jpg)
![Free Printable Stock Ledger Templates [Excel,PDF, Word] 3 Stock Ledger](https://www.typecalendar.com/wp-content/uploads/2023/08/Stock-Ledger-150x150.jpg)
